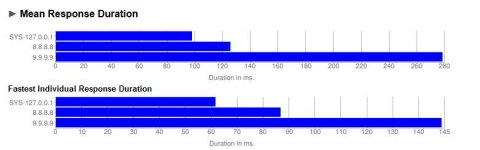
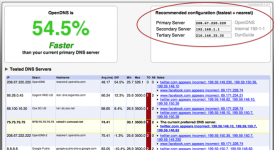
Thanks for the info but I wish I understood all the details more, just like when I was trying to understand how some stuff works as in the article I was reading earlier:
“Suspicious” event routes traffic for big-name sites through Russia
https://arstechnica.com/information...es-traffic-for-big-name-sites-through-russia/
- Patrick
======
Why the Quad 9 will not work for most is simple... The ISPs will redirect Quad 9 DNS queries to their local DNS server. Doing so will save bandwidth for their internet connections. Yes, the ISPs DNS servers will send out the DNS query to the internet, but it's a single server and and not hundreds of thousands of customers doing the same.
The bandwidth savings will come from locally caching the DNS server's query results and serving it up to the customers accessing the same sites. The ISPs DNS server already have the response in the cache, no need to query the internet. It's very similar to what your DNS client does on your system. It does not query the
www.mac-forums.com all the times, when you browse this forum. The DNS client already has a resolution for that.
Could the ISPs DNS server utilize Quad9 server for their queries? They absolutely could, but they probably won't. People, who cannot access black listed sites by Quad9 servers will call. Support is costly and better off just allow the connection, instead of blocking it.
The Arstech article about suspicious routing is more complex. The following may or may not be a simple explanation...;D
You have an address where you live and people know where to send mail to you. It is true that you gave them your address, including ZIP-code. The post office, UPS, FEDEX, etc., use the ZIP-code to route the mail to your town, where it is sorted by ZIP-code/address and delivered to you.
Let's say that friend of yours asked by someone where to send mail to you and he/she intentionally/unintentionally gives the wrong address, ZIP-code. In this case, the mail will end up at the wrong address.
Let's say that I live somewhere close by and go to your post office and pretend to be you. I'll ask for a change of address form for you and file it with the post office. Since the post office did not detect the false identity, it'll dutifully forward your mail to the address I specified in the form that could actually be my address.
In the case of the internet traffic, the Autonomous System (AS) is pretty much equivalent to ZIP-code. Except instead of street addresses, the AS deals with IP addresses.
The AS39523 in the article advertised through Border Gateway Protocol (BGP) the block of IPs, it claimed to know how to route requests to these IPs. Other routers on the internet with BGP enabled took notice of the new route and accordingly, forwarded IP addresses to the AS39523's router. Once they got there, they were probably routed to the rightful destination, but in the meantime, all the pockets flowing through the AS39523 router could have been captured and analyzed later.
Yes, that's how vulnerable the Autonomous System is. While there's a verification process for obtaining an AS number for a block of IP addresses, there's no verification process in place for changing the AS router advertised block of IP addresses. If I own a small block of IPs and get an AS number and BGP router, I can advertise route for any blocks of IP addresses.
The AS39523 router advertisement could have been unintentional, network administrator error, or intentional with a purpose. This is not the first, nor it is the last time when the AS incorrectly claiming to know how to route a block of IP addresses. But... Since it is an Autonomous System in Russia and the current phobia in the US about Russia, everyone is convinced that this had been intentional. I am not convinced for a number of reasons...





 If I am a hacker, guess where I'll have my malware distributed from?
If I am a hacker, guess where I'll have my malware distributed from?